Getting in touch with Quality: Neighborhood Managed Service Providers Near Me
Strategize and Range WITh Proven IT Managed Solutions Strategies
In the fast-paced landscape of modern-day company, the strategic application of IT handled services has actually ended up being a cornerstone for companies aiming to enhance functional efficiency and drive lasting growth. By implementing tried and tested methods tailored to fulfill particular business requirements, companies can browse the complexities of modern technology while staying dexterous and competitive in their corresponding markets. As the need for scalable IT services remains to increase, recognizing how to properly strategize and utilize managed solutions has actually never been a lot more crucial. It is within this world of innovation and optimization that services can truly unlock their possible and lead the method for future success.
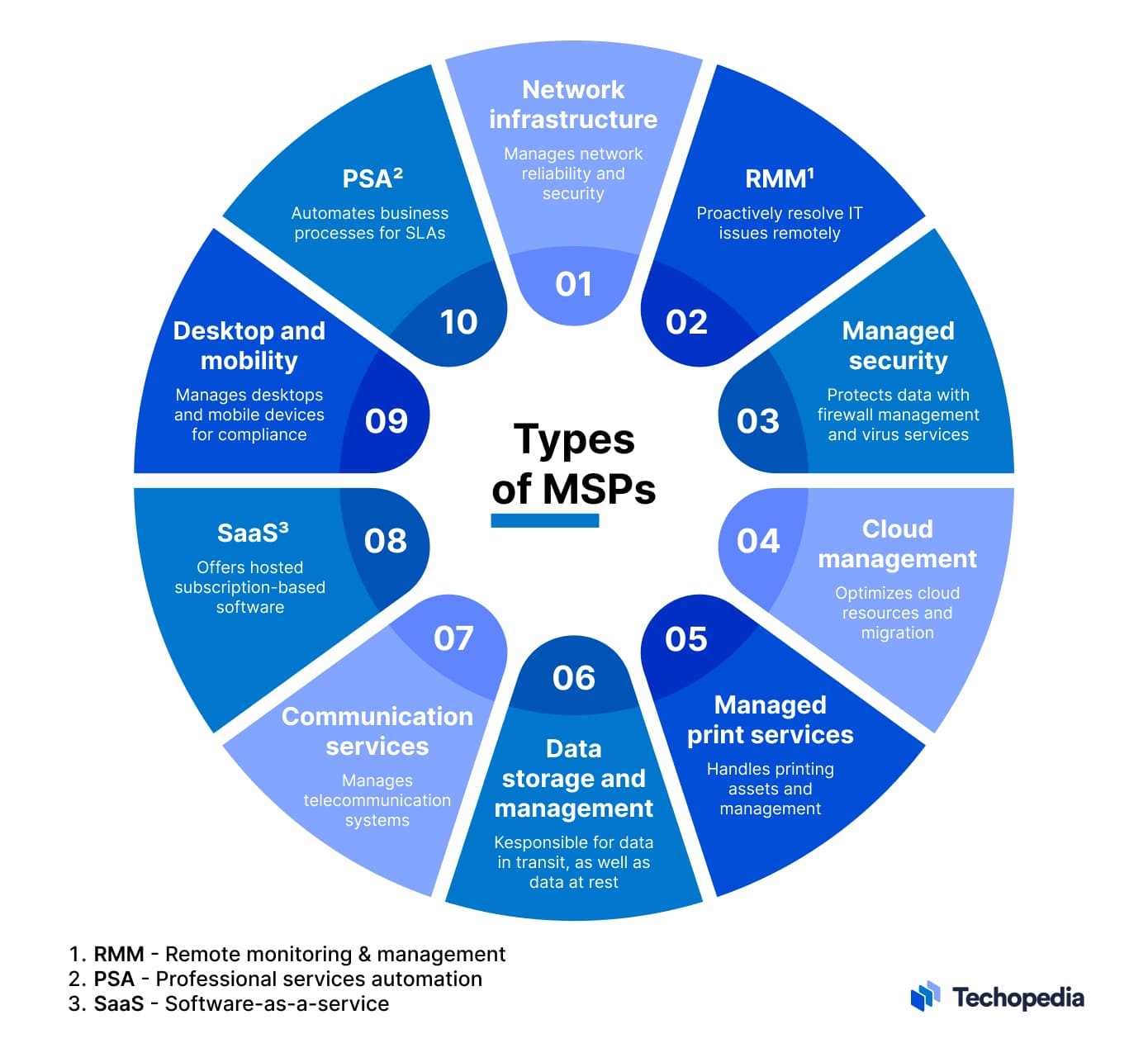
Benefits of IT Managed Solutions
By outsourcing IT management to a specialized service provider, businesses can tap right into a riches of know-how and resources that would or else be expensive to maintain internal. One of the crucial advantages of IT Took care of Provider is positive monitoring and upkeep of systems, which assists avoid possible problems before they rise into significant issues.
This makes sure that organizations remain affordable in a swiftly evolving technological landscape. In final thought, the advantages of IT Managed Services are important in enhancing procedures, boosting effectiveness, and eventually, driving organization success.
Key Techniques for Implementation
With an understanding of the substantial benefits that IT Took care of Services offer, organizations can now concentrate on implementing vital strategies to efficiently incorporate these solutions into their procedures. One crucial technique is to clearly specify the scope of services required. This involves conducting an extensive analysis of existing IT infrastructure, identifying pain points, and establishing details goals for enhancement. Additionally, services must establish clear interaction channels with their handled provider to make sure smooth cooperation and prompt problem resolution.
An additional crucial approach is to focus on cybersecurity steps. Data violations and cyber threats pose significant dangers to companies, making safety and security a leading concern. Executing robust security procedures, normal tracking, and prompt updates are vital action in safeguarding sensitive information and keeping service continuity.
Additionally, businesses need to establish solution level arrangements (SLAs) with their handled service company to define assumptions, duties, and performance metrics. SLAs aid in establishing clear standards, guaranteeing liability, and maintaining service high quality criteria. By integrating these key methods, organizations can leverage IT Took care of Provider to streamline operations, improve performance, and drive lasting development.
Making The Most Of Efficiency Through Automation

Moreover, automation makes it possible for real-time surveillance and information evaluation, providing valuable insights for educated decision-making. By automating routine surveillance tasks, businesses can proactively address concerns before they escalate, minimizing downtime and enhancing efficiency (msp association of america). Additionally, automation can help with the seamless assimilation of various systems and applications, improving cooperation and data flow throughout the organization
Ensuring Information Security and Conformity
Information security and conformity are critical problems for organizations running in the electronic landscape of today. With the enhancing volume of sensitive data being saved and processed, guaranteeing durable safety measures is important to guard versus cyber hazards and stick to regulative demands. Executing detailed data safety practices entails securing data, developing accessibility controls, routinely upgrading software program, and carrying out protection audits. Additionally, adhering to policies such as GDPR, HIPAA, or PCI DSS is important to maintain and avoid costly charges depend on with consumers. Managed IT companies play a crucial function in assisting businesses navigate the facility landscape of data security and conformity. They provide competence in carrying out security methods, keeping track of systems for prospective violations, and ensuring adherence to sector his comment is here guidelines. By partnering with a trustworthy handled companies, services can boost their information security position, reduce dangers, and show a commitment to safeguarding the discretion and honesty of their information properties.
Scaling IT Facilities for Growth
Integrating scalable IT infrastructure options is vital for facilitating company growth and operational performance. As firms increase, their IT requires evolve, calling for infrastructure that can adapt to boosted needs flawlessly. By scaling helpful resources IT facilities properly, companies can guarantee that their systems remain reliable, safe and secure, and performant even as work expand.
One trick element of scaling IT infrastructure for growth is the ability to flexibly designate sources based on existing needs. Cloud computing solutions, for example, deal scalability by permitting businesses to change storage space, processing power, and various other resources as needed. This elasticity allows firms to effectively take care of spikes sought after without over-provisioning resources during periods of reduced task.
Additionally, executing virtualization innovations can boost scalability by making it possible for the production of virtual instances that can be easily duplicated or modified to fit altering workloads - managed service provider. By virtualizing servers, storage, and networks, organizations can maximize source utilization and enhance IT monitoring processes, inevitably sustaining business growth initiatives effectively
Final Thought
To conclude, executing IT took care of solutions can bring many benefits to a company, such as enhanced effectiveness, boosted data safety and security, and scalability for development. By adhering to key techniques for implementation, using automation to maximize efficiency, and making certain data safety and security and compliance, organizations can better plan and scale their IT facilities. It is vital for companies to adapt and advance with technical innovations to stay competitive in today's ever-changing landscape.